Project Documentation
Architecture decisions, configurations, and troubleshooting logs for sedky.net
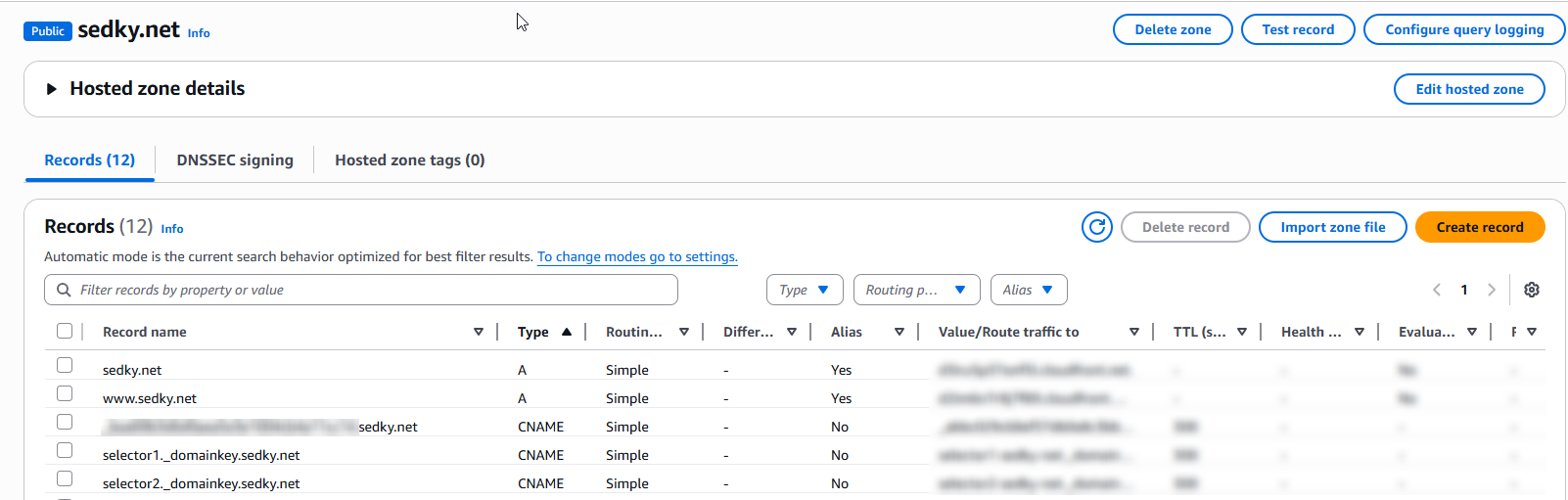
1. Route 53 DNS Setup
I registered and managed the sedky.net domain using Amazon Route 53. To validate Microsoft 365 email, I added:
- 2 CNAME records for DKIM
- 1 TXT record for SPF
- 1 TXT record for DMARC
Issue encountered: Route 53 automatically appended .com to the CNAME values provided by Microsoft, causing DKIM validation to fail. The fix was to re-enter the exact value without the suffix.
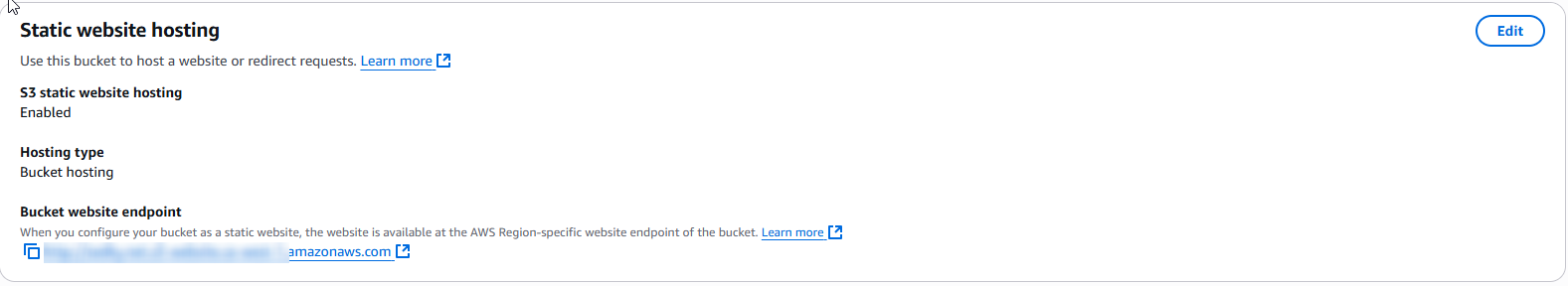
2. S3 Static Website Hosting
The portfolio is hosted on Amazon S3 using the static website hosting feature. This approach is:
- Fully serverless
- Highly cost-effective
- Eligible under AWS free tier
This allows static content to be delivered globally with no backend server or EC2.
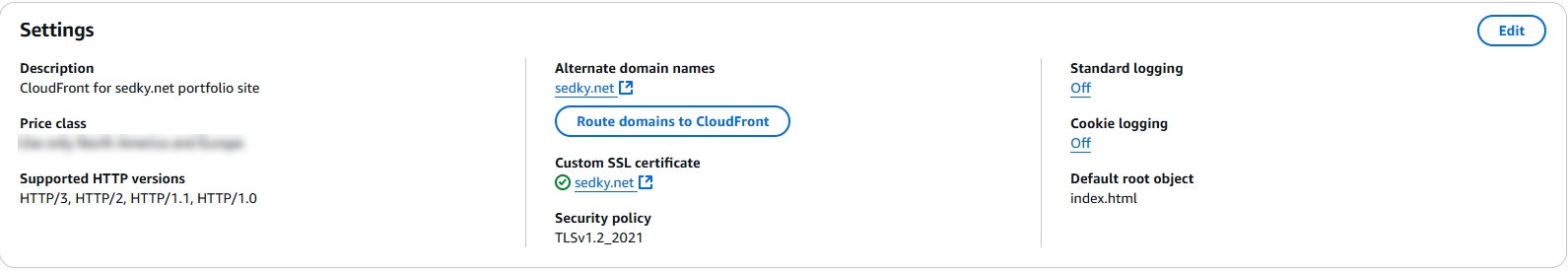
3. CloudFront CDN + HTTPS + ACM Certificate
To deliver secure, fast-loading content globally, I configured AWS CloudFront as the CDN layer for sedky.net. It caches my static website across edge locations and provides automatic HTTPS via an SSL certificate from AWS Certificate Manager (ACM).
- CloudFront Origin: The origin is set to the S3 static hosting endpoint
- Alternate Domain Name (CNAME): sedky.net
- SSL/TLS Certificate: Issued via ACM in
us-east-1and attached to CloudFront - HTTPS support: Enforced using
TLSv1.2_2021security policy
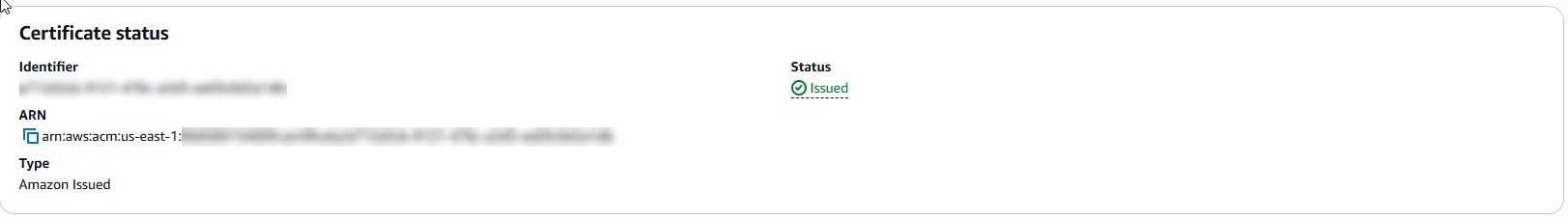
✅ SSL Certificate Status
The SSL certificate was requested through AWS Certificate Manager and validated using DNS in Route 53. Once validation completed, the certificate was marked as "Issued" and applied to the CloudFront distribution.
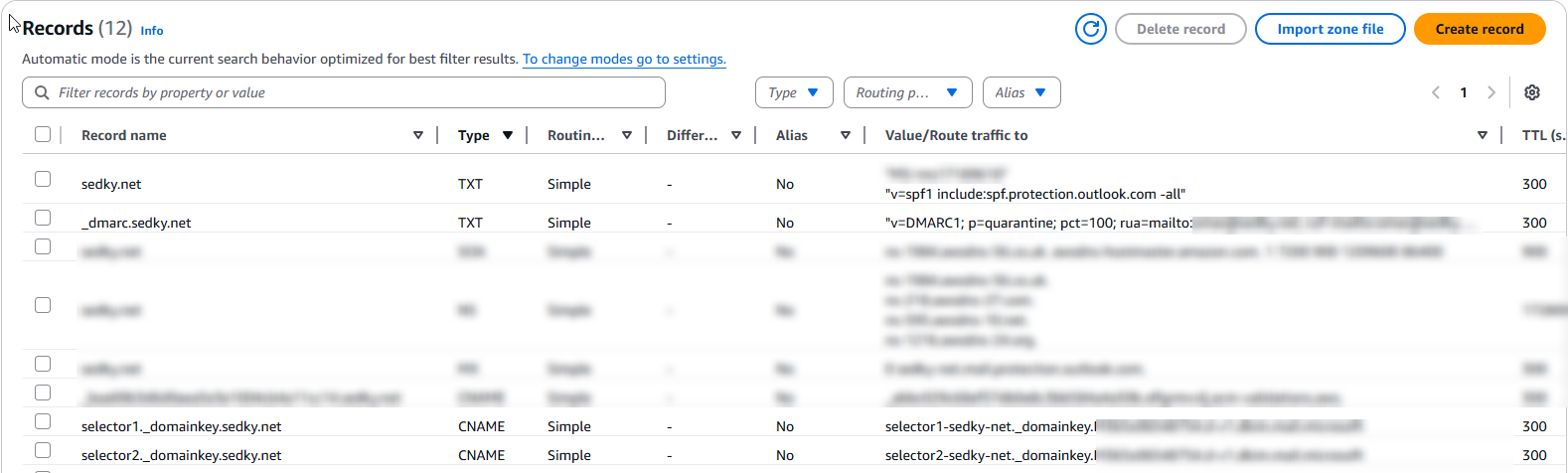
4. DNS + Email Deliverability (SPF, DKIM, DMARC)
I configured Microsoft 365 email for sedky.net and manually added SPF, DKIM, and DMARC DNS records in Route 53. This ensured high deliverability and proper domain authentication — critical for professional communication and AWS recruiter visibility.
- SPF: TXT record with Outlook protection domain
- DKIM: 2 CNAME records (selector1 + selector2)
- DMARC: TXT record with policy set to
p=quarantine
Issue encountered: Route 53 auto-appended .com to the DKIM CNAME values during record entry. The fix was to paste the record value exactly as provided by Microsoft, without any trailing suffix.
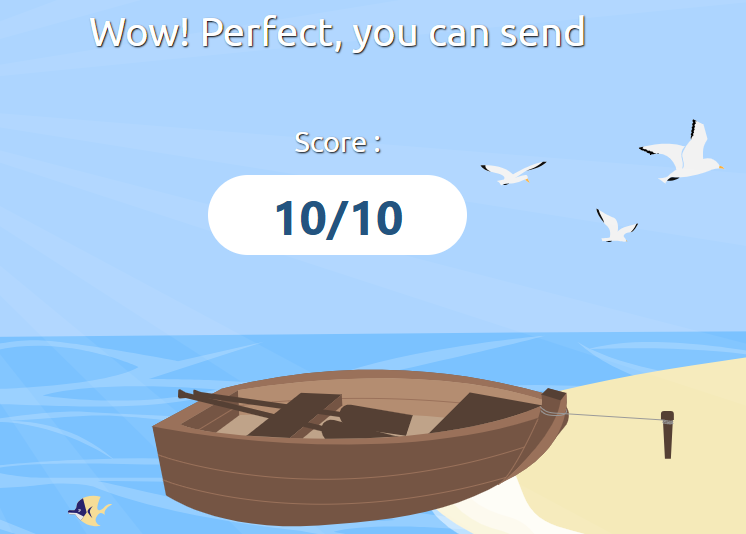
📨 Deliverability Test (mail-tester.com)
I validated all DNS records using mail-tester.com and achieved a perfect score of 10/10. Headers confirmed alignment across SPF, DKIM, and DMARC.
5. Architecture Value & GitHub Documentation
This project demonstrates not just AWS technical ability, but real-world infrastructure problem-solving:
- ✅ Precision DNS troubleshooting with DKIM/DMARC resolution
- ✅ Cloud-native architecture (S3 + CloudFront + ACM + Route 53)
- ✅ Enterprise-grade email authentication via Microsoft 365
- ✅ Clean and scalable infrastructure, fully automated and cost-efficient
Full implementation steps, configurations, and validation notes are publicly documented on GitHub:
📘 View Full GitHub Documentation