Project Documentation
Multi-Cloud Flask App with MongoDB Atlas (AWS, Azure, GCP)
This project showcases the deployment of a containerized Flask app across three cloud providers using a centralized MongoDB Atlas backend with secure, environment-based credential handling.
1. Problem Statement
Deploying applications across multiple cloud providers introduces complexity in networking, secrets management, and deployment flow. This project addresses the need for portable, secure, and repeatable deployment of a web app using a shared database across AWS, Azure, and Google Cloud.
2. Architecture Overview
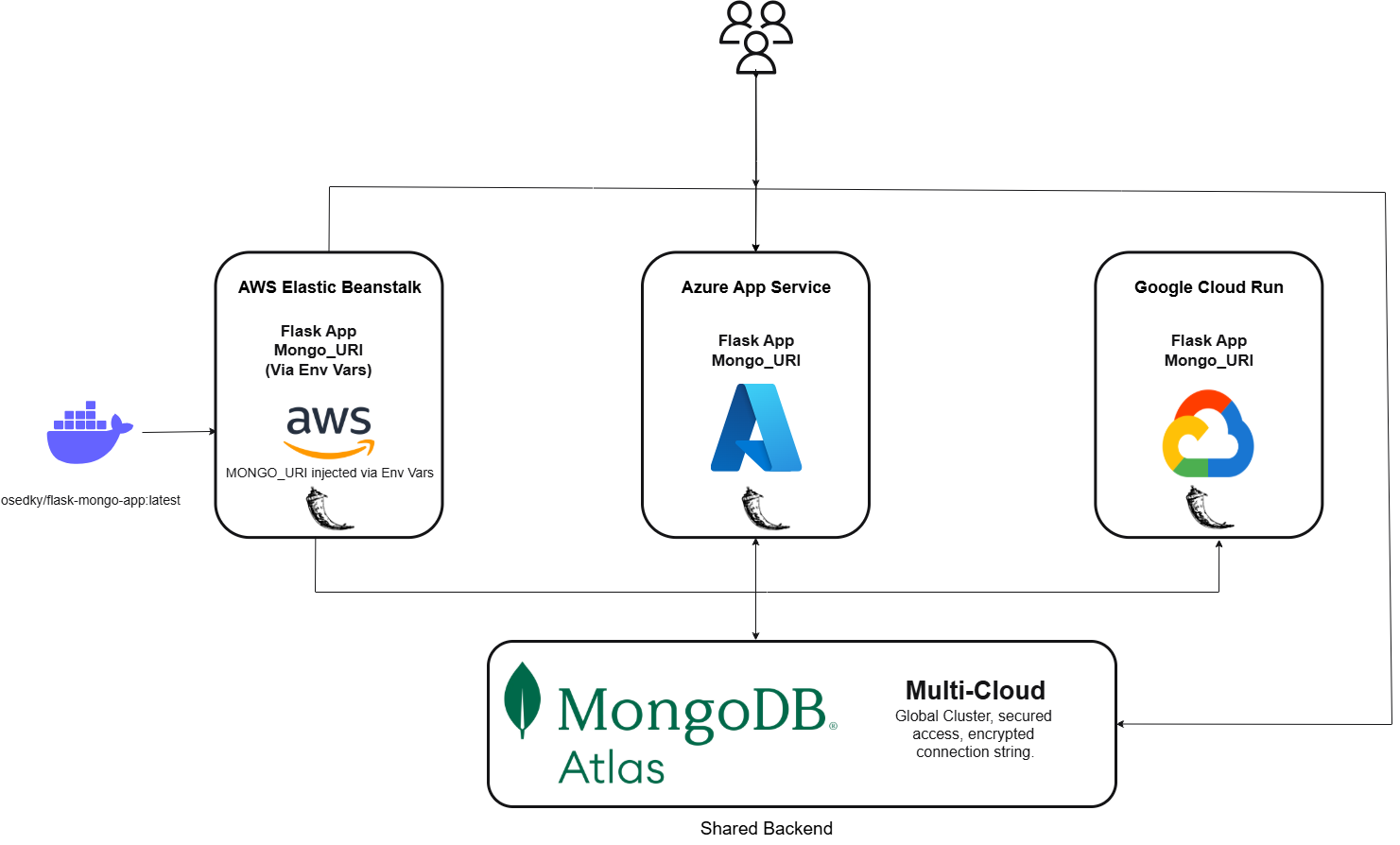
Containerized Flask app deployed via Docker on three providers, using centralized Atlas backend and injected secrets.
3. Step-by-Step Implementation
- Create and provision a MongoDB Atlas multi-cloud cluster
- Build Docker container and push image to Docker Hub
- Deploy on Google Cloud Run using gcloud CLI
- Deploy on Azure App Service via Docker Hub
- Deploy on AWS Elastic Beanstalk using Dockerrun.aws.json
- Inject MONGO_URI through environment variables on each platform
- Use .env templating to handle secrets cleanly
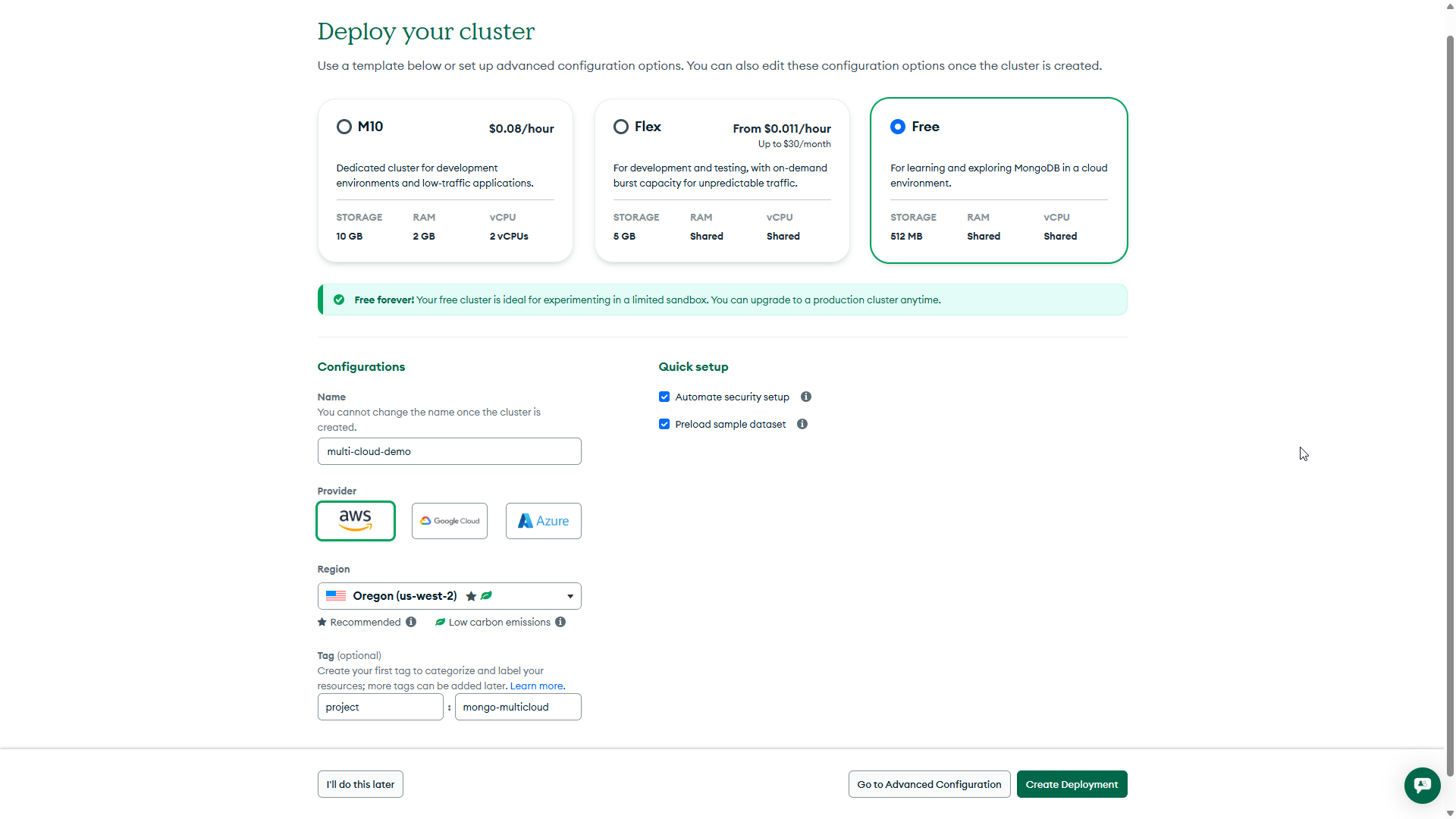
Initial Atlas cluster configuration across regions.
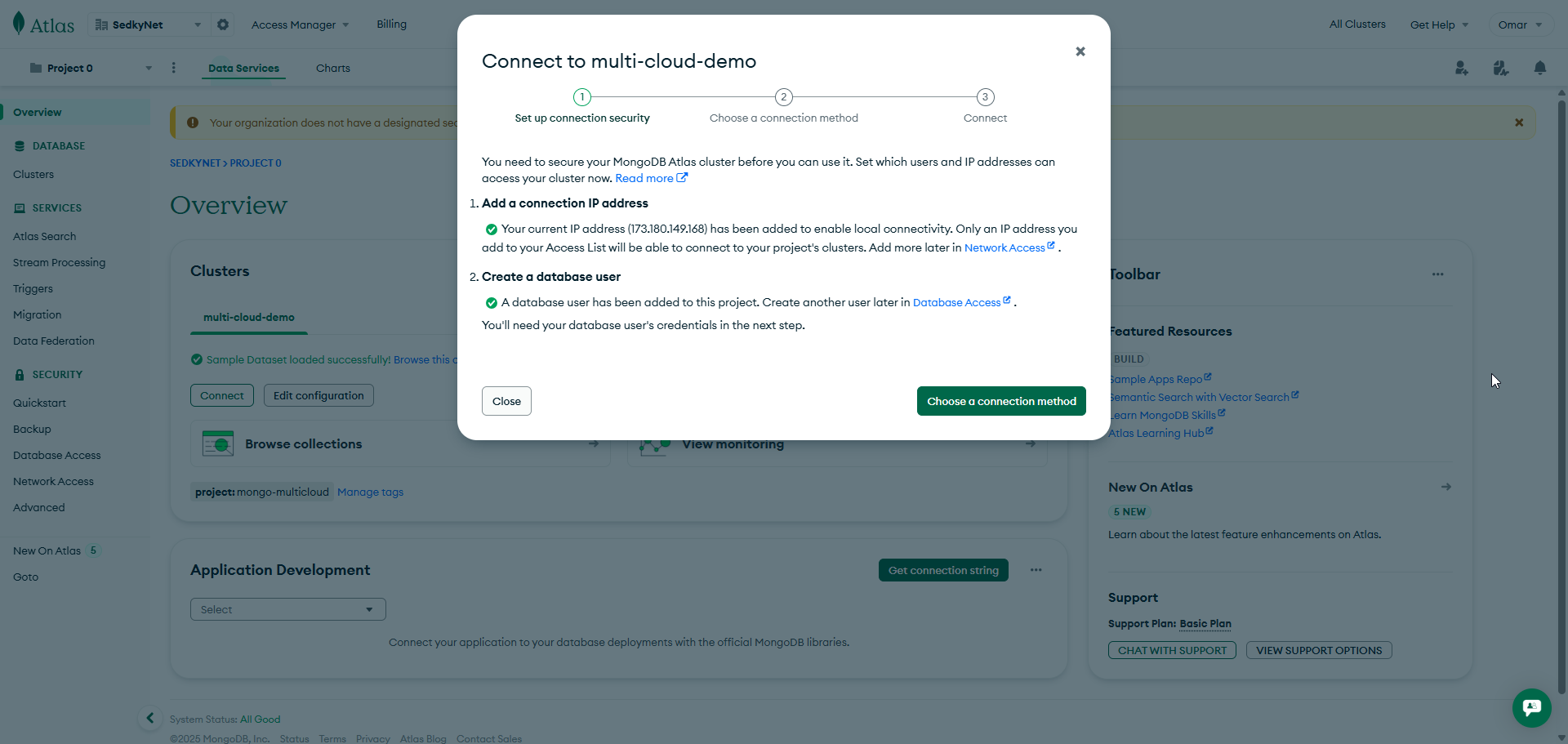
Cluster provisioned and ready for external application connection.
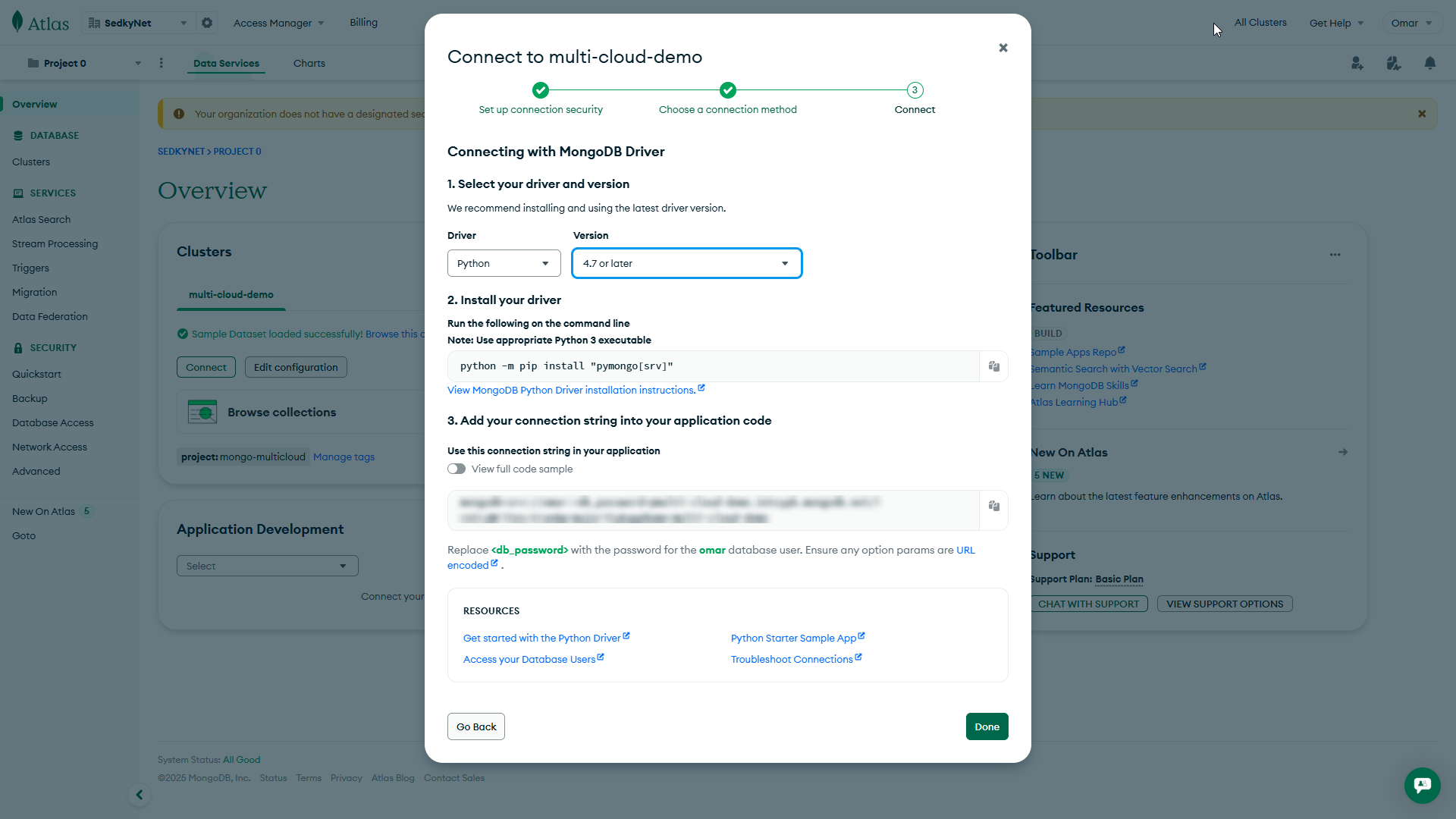
Copy secure connection string for app integration.
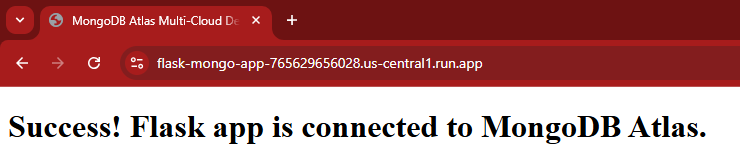
Successful deployment to GCP Cloud Run using container image and env vars.
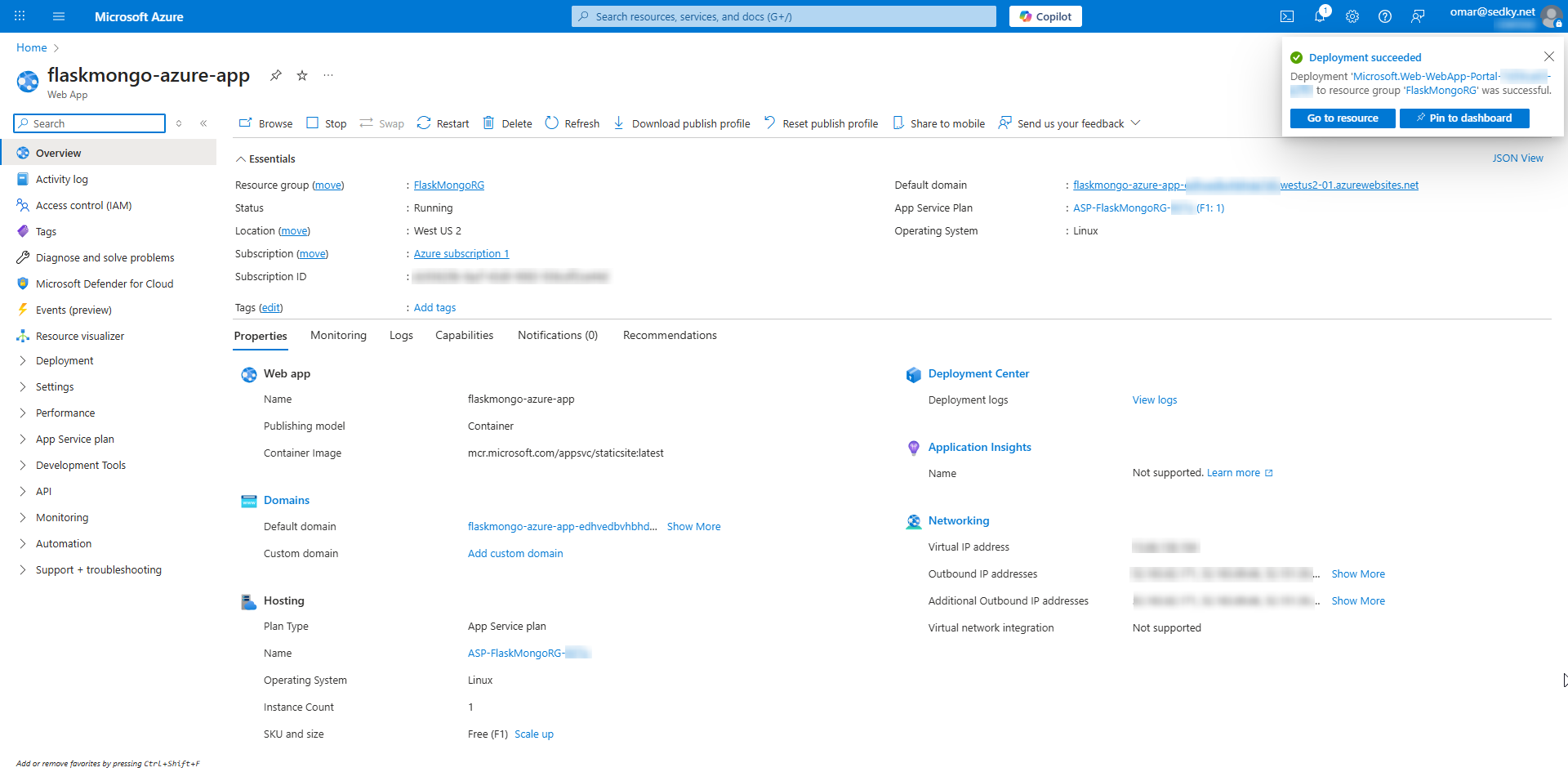
Flask container deployed and verified on Azure App Service via Docker Hub.
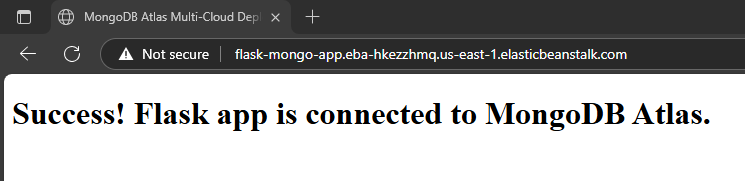
Deployment on Elastic Beanstalk using Dockerrun.aws.json and .env config.
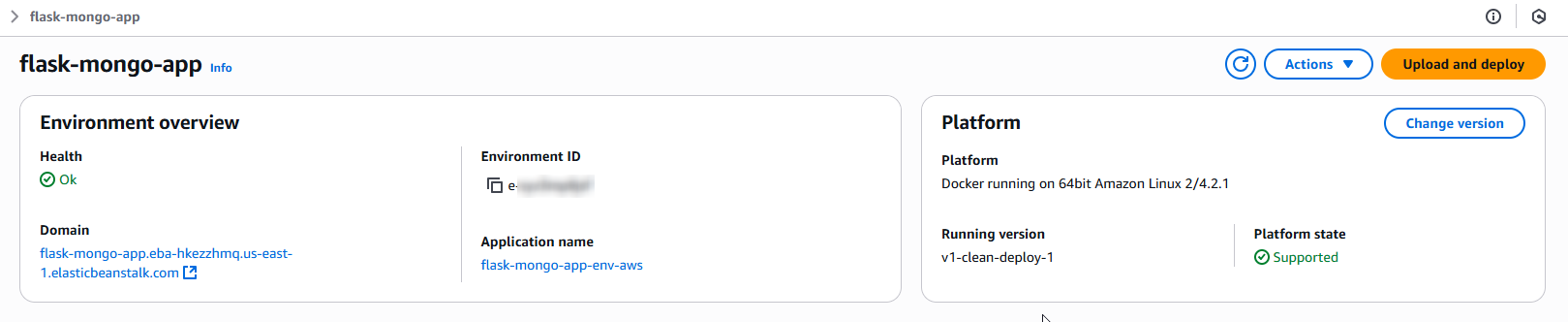
Elastic Beanstalk environment running v1-clean-deploy-1 on Amazon Linux 2 Docker platform. Health check passed and public domain is active.
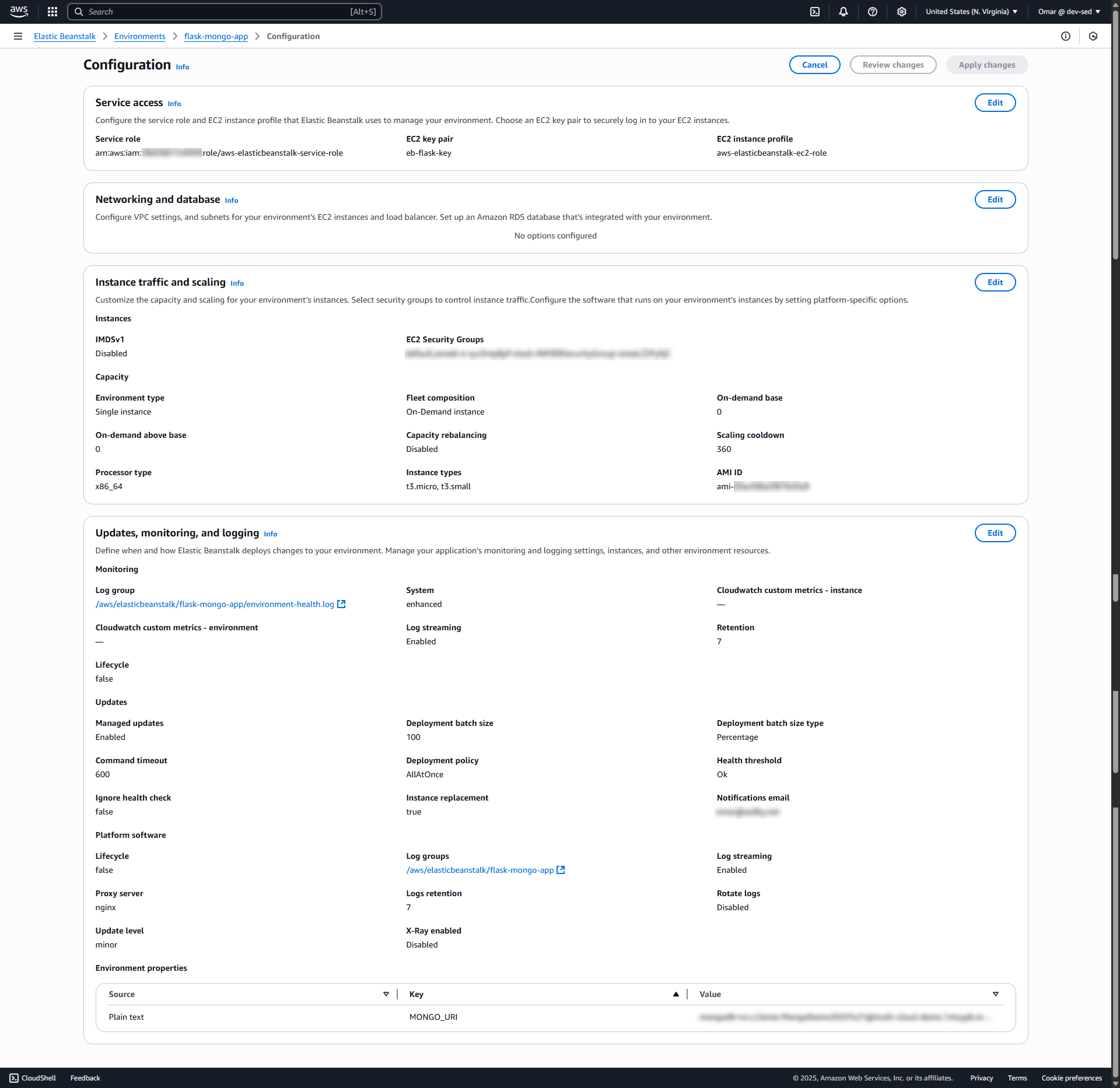
AWS configuration includes IAM role, EC2 instance details, logging, and injected Mongo URI variable confirming secure deployment.
4. Security & CI/CD Design
- Environment variables used for all secrets and URIs
- No secrets stored in Docker image
- GitHub repo sanitized from ZIPs and plain configs
- CI handled manually but supports future automation
- Elastic Beanstalk logging and health checks enabled
5. AWS Well-Architected Framework Alignment
- Operational Excellence: Container tested in 3 cloud environments
- Security: Externalized secrets, IAM policies enforced
- Reliability: Validated health and runtime across providers
- Performance Efficiency: Lightweight, auto-scaling ready
- Cost Optimization: Deployed using free-tier in all 3 providers
6. Challenges & Resolutions
- Secrets leak in repo ZIP: Resolved with .env usage and cleanup
- Azure App Service timeout: Resolved by container registry caching
- Elastic Beanstalk config errors: Corrected Dockerrun and environment mapping
7. Summary & Business Impact
This project demonstrates production-aware, portable application design across multiple clouds. It highlights real-world CI/CD adaptability and security handling through secrets externalization.