Project Documentation
Federating AWS Console Sign-in with Microsoft Entra ID & Conditional Access
This project demonstrates a robust solution for integrating AWS Console access with Microsoft Entra ID using SAML 2.0 federation and Conditional Access. It addresses real-world identity management requirements with security-first design and automation.
1. Problem Statement
In modern enterprises, centralized identity management is critical for secure access control across cloud environments. Many organizations rely on Microsoft Entra ID (Azure AD) as their primary Identity Provider. This project solves the challenge of federating AWS sign-in using SAML 2.0 while enforcing Conditional Access policies such as MFA and group-based role mapping.
2. Architecture Overview
- Microsoft Entra ID (Azure AD) as SAML Identity Provider
- AWS IAM Identity Provider + IAM Roles with Trust Policies
- Security Groups to control access levels
- Conditional Access policy enforcing MFA and trusted location access
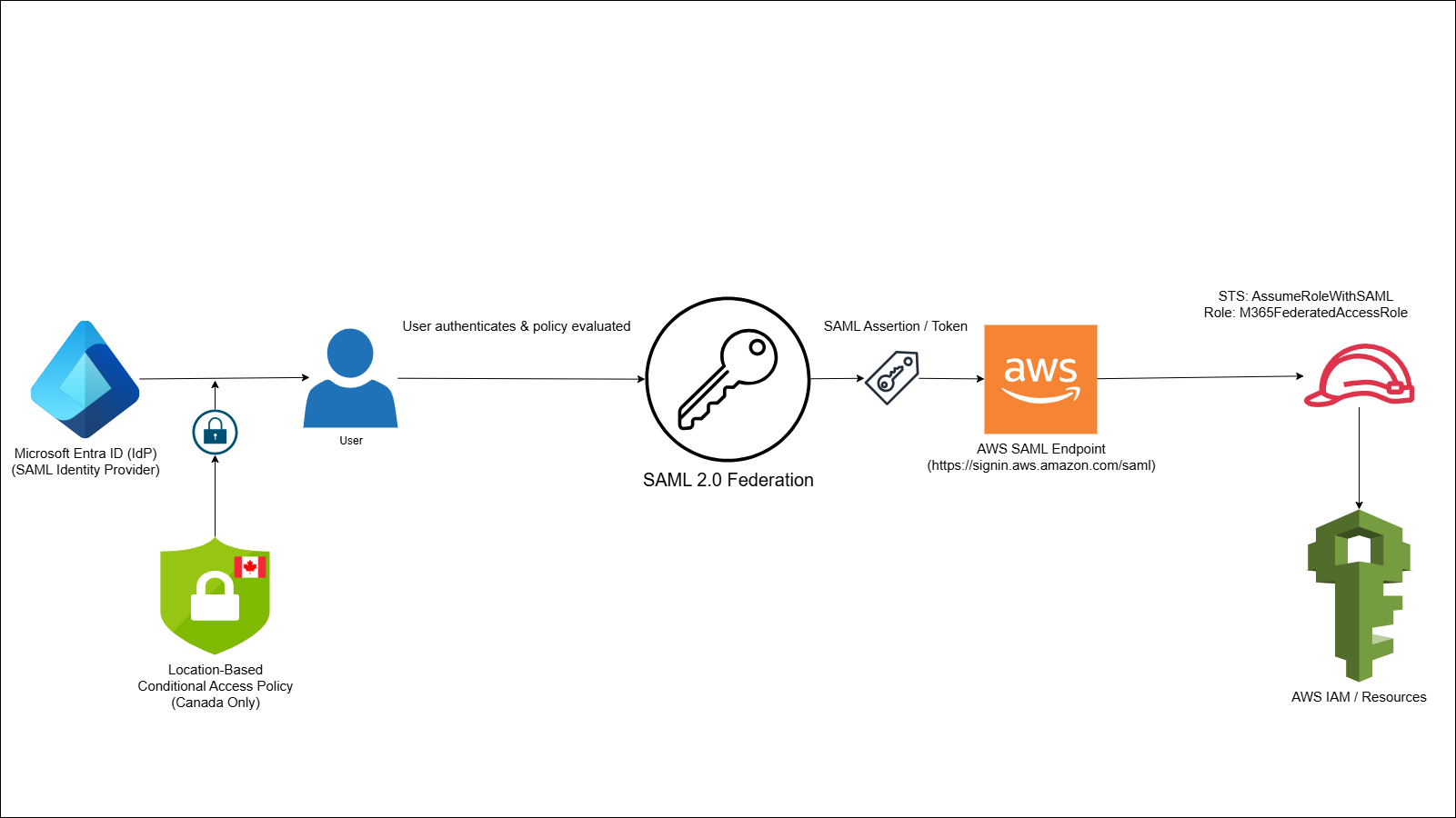
Federation flow: Entra ID evaluates Conditional Access and issues SAML assertion to AWS with trusted role assumption.
3. Step-by-Step Implementation
- Create a dedicated user in Microsoft 365 for federation
- Define security groups for access control
- Register AWS app in Microsoft Entra ID as Enterprise App
- Configure basic SAML settings and group-based claims
- Download and save the Federation Metadata XML
- Create IAM Identity Provider in AWS Console
- Create IAM Role with group-based trust policy
- Configure Conditional Access policy targeting AWS app
Screenshots from each step are provided below.
User created for federated authentication. MFA and policy applied through Entra ID.
Security group created for role-based access to AWS.
Enterprise application registered with AWS-specific SAML endpoints.
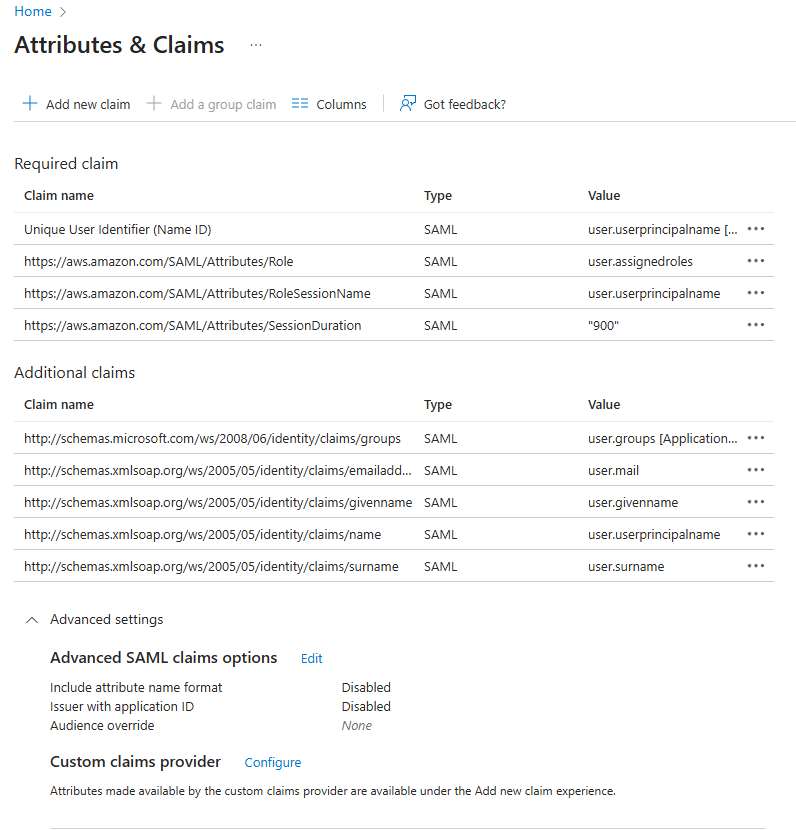
Group claim issued to drive access control in IAM trust policy.
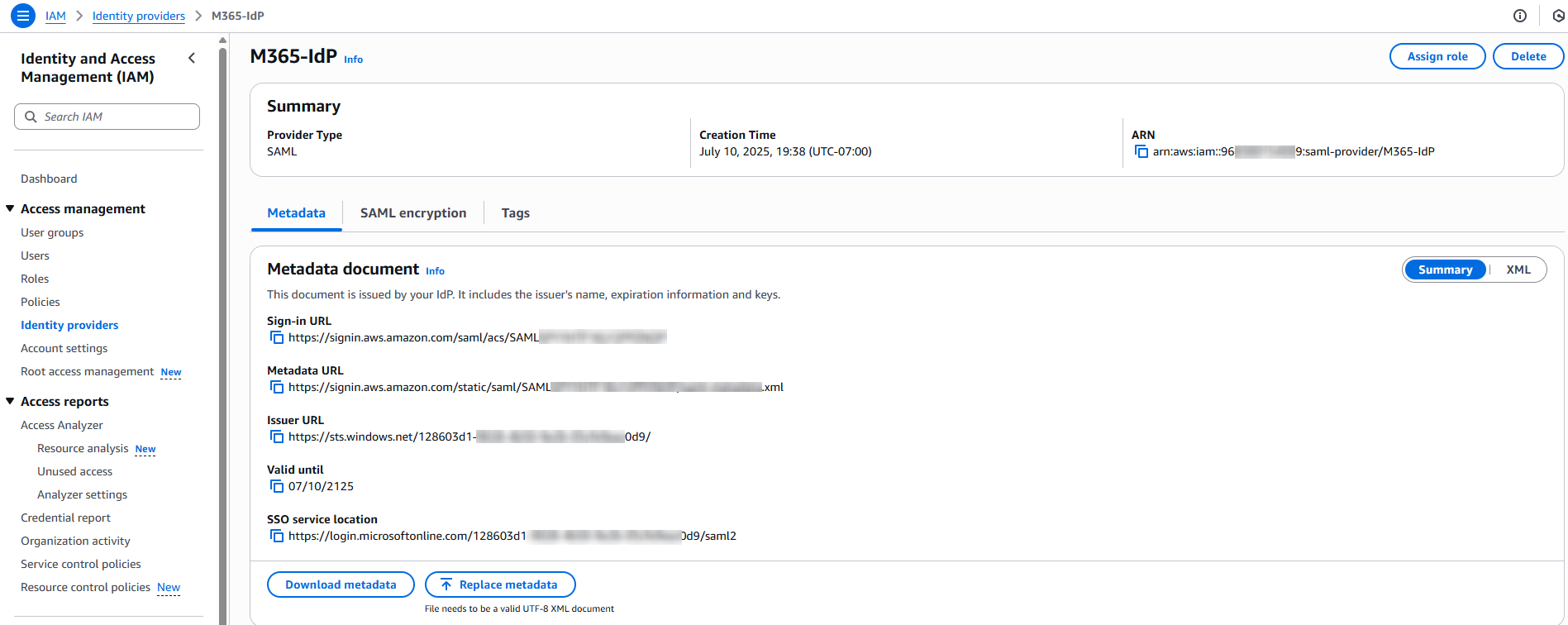
IAM Identity Provider created in AWS using downloaded metadata from Entra.
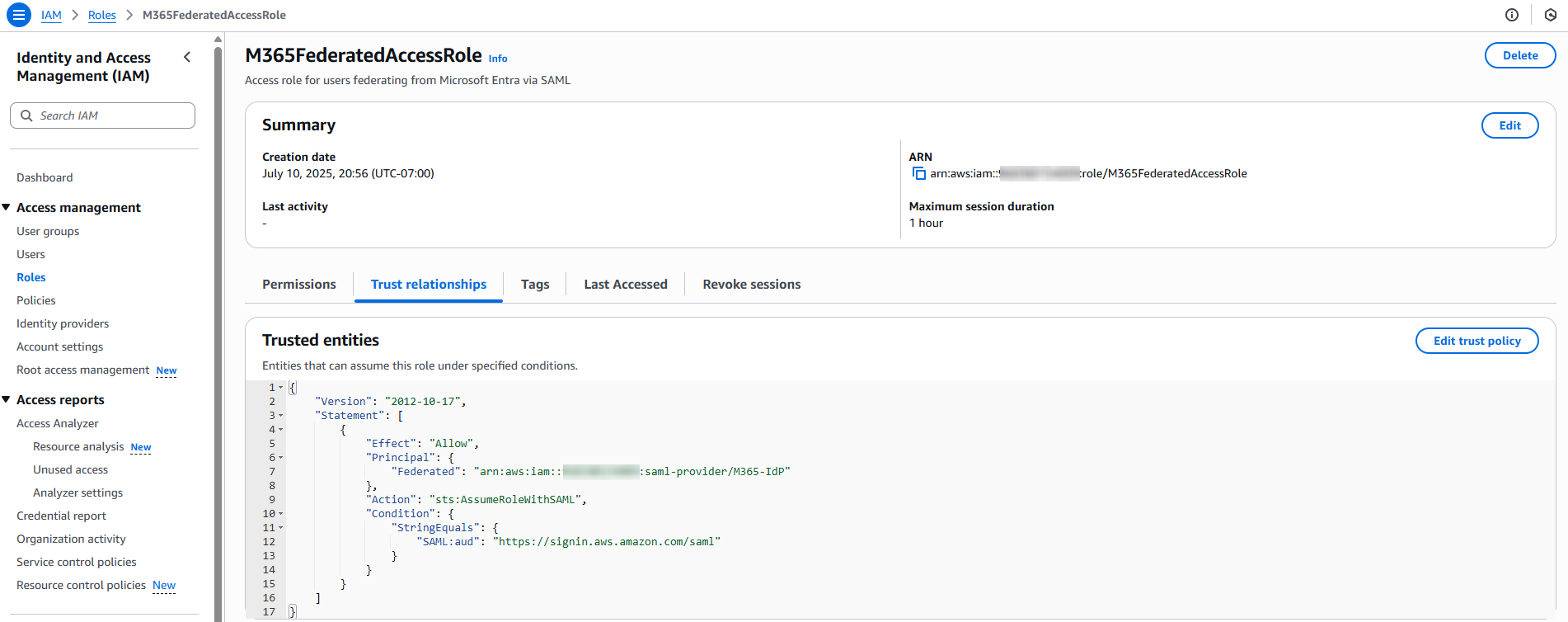
Role created for federated users. Access governed by trust and group claims.
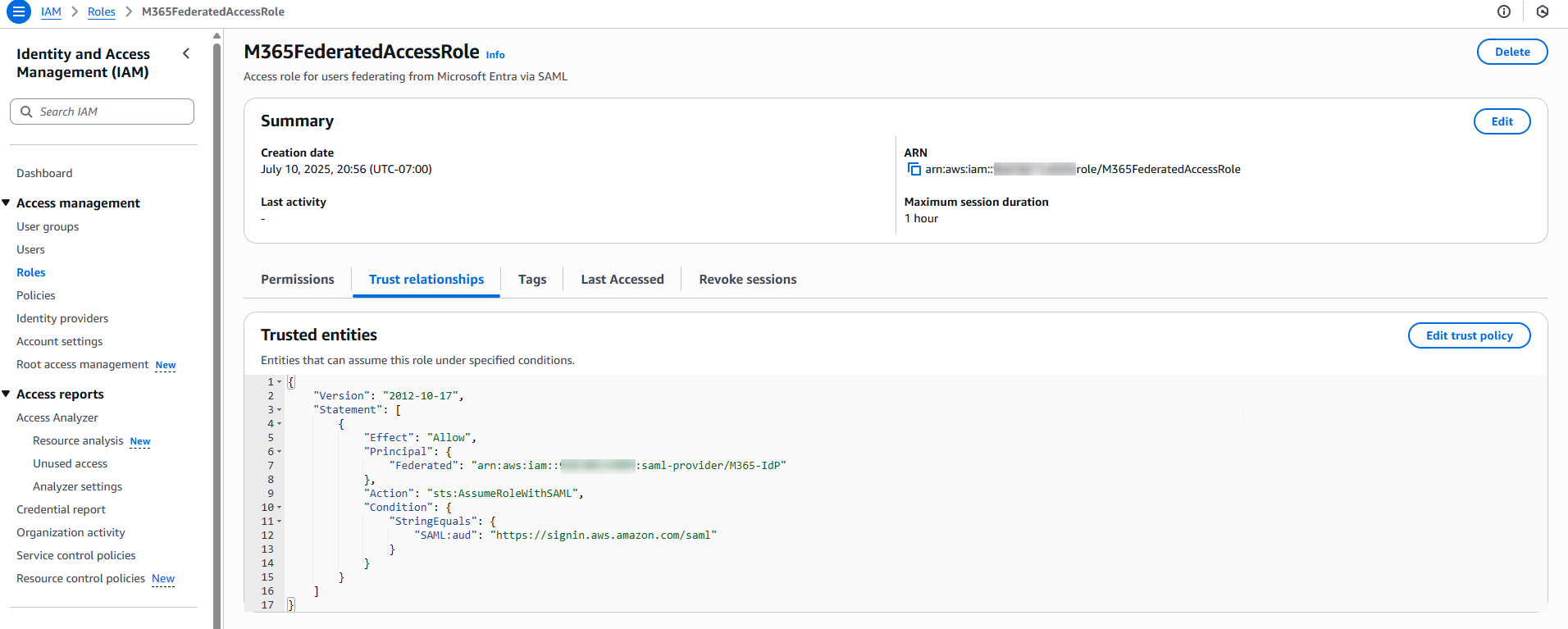
Trust policy specifies SAML provider and group claim for access grant.
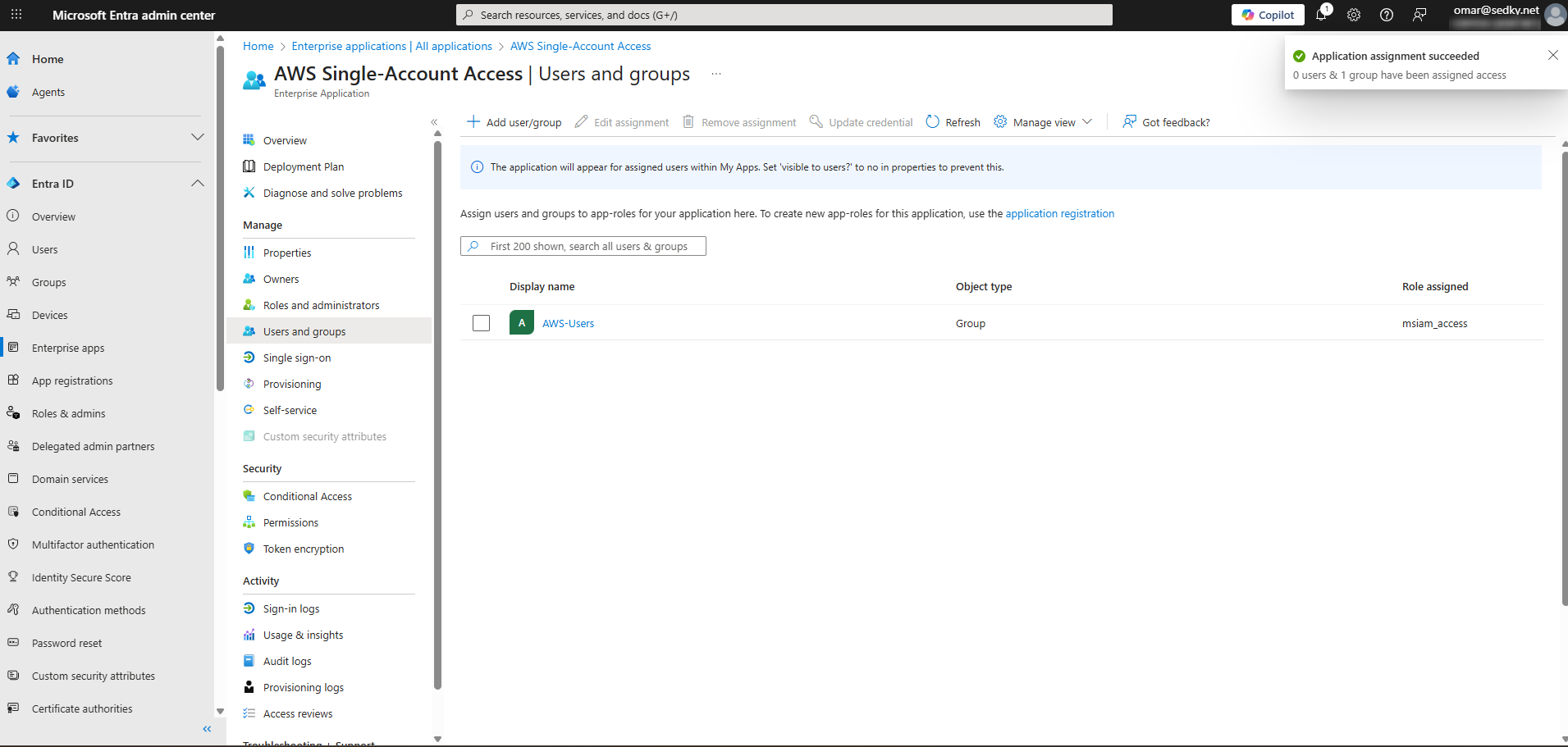
Group assignment mapped to AWS Enterprise App for scoped access.
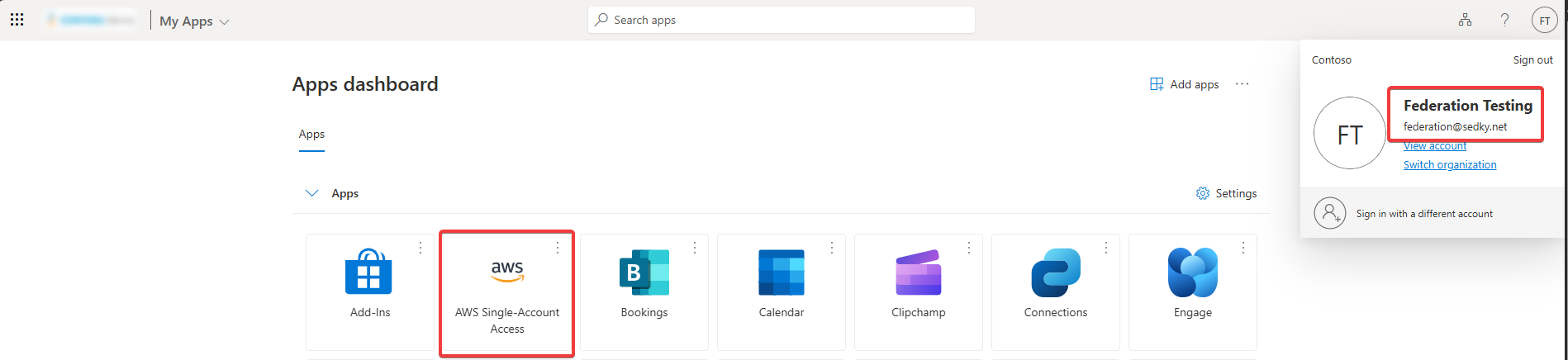
User initiates SSO login through MyApps portal.
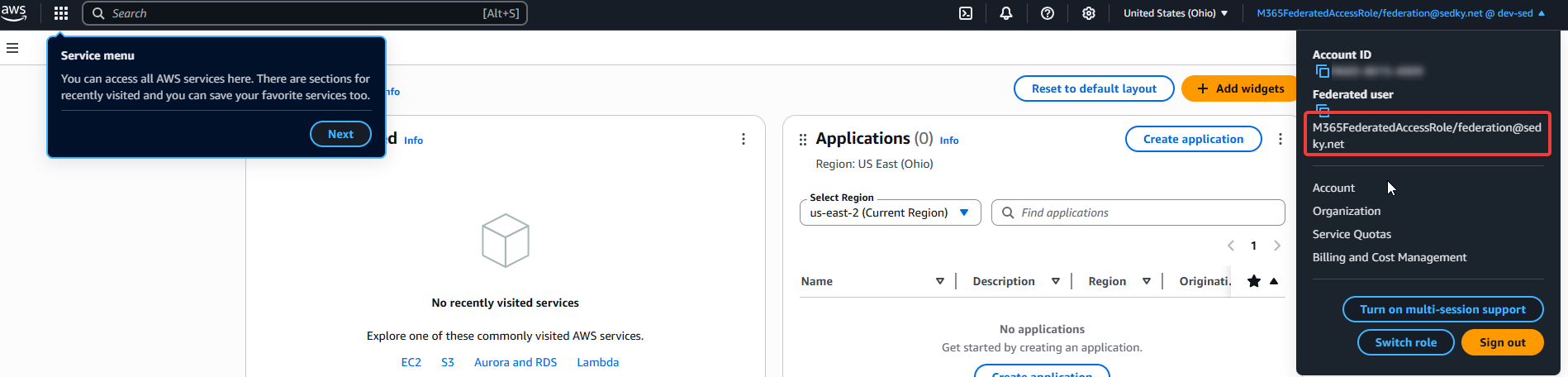
Federated user lands in AWS Console with correct assumed role.
4. Conditional Access – Trusted vs. Untrusted Location
The Conditional Access policy was configured with the following criteria:
- Targeted application: AWS Enterprise App
- Assigned group: AWS-Users security group
- Grant control: Require MFA
- Named Location: Trusted IPs from Canada only
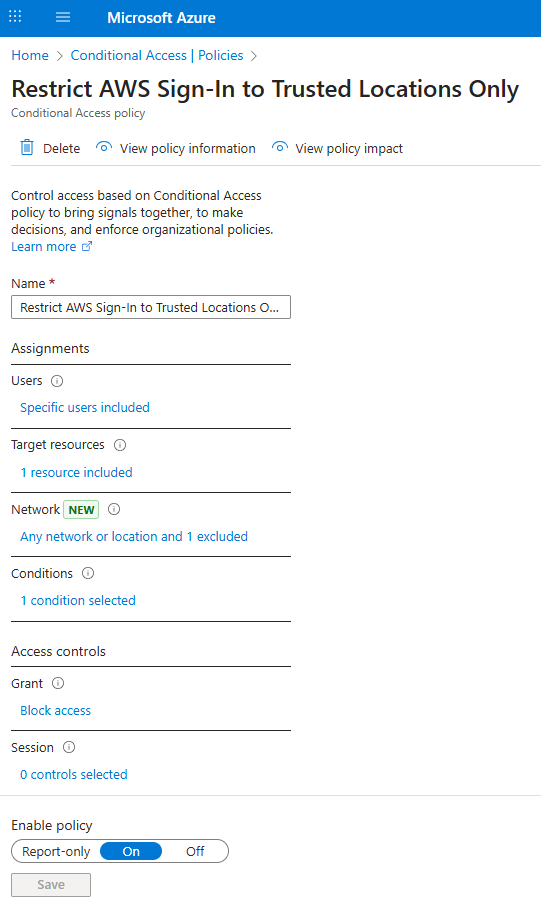
Named location policy allowing access only from Canadian IP ranges.

Policy includes specific group and resource restrictions, enforced through location filter.
Login testing confirmed enforcement:
- Trusted: Canada IP → successful login
- Untrusted: VPN from US → access blocked
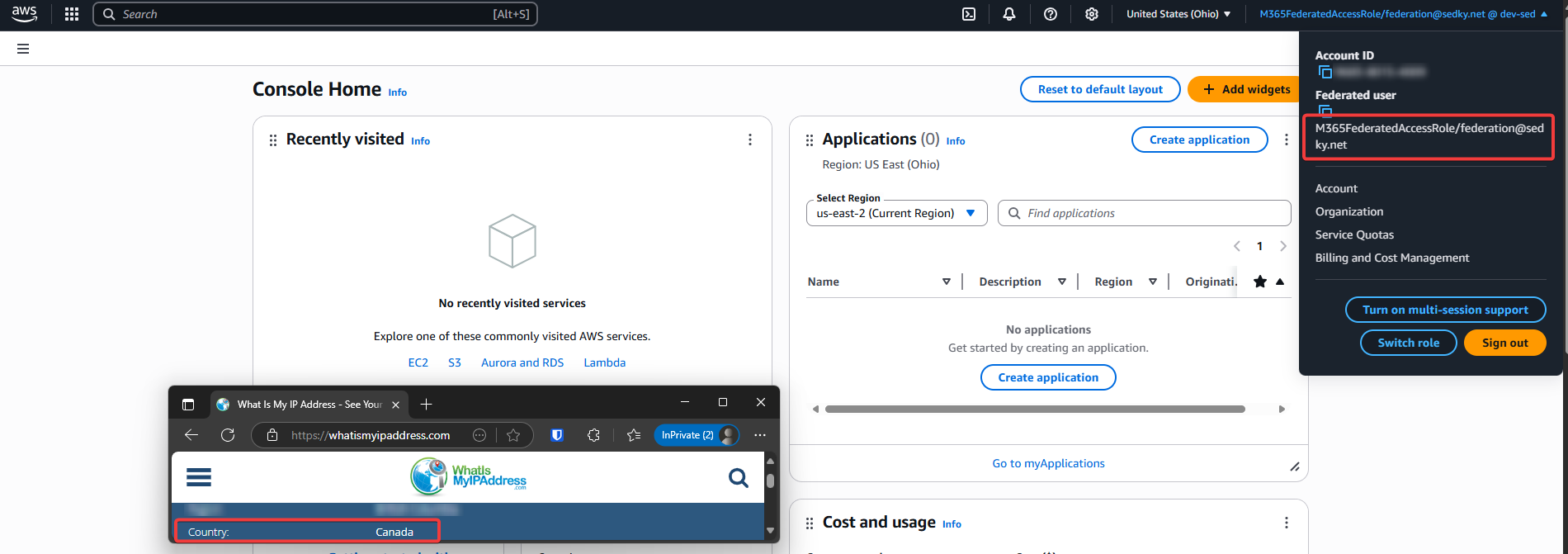
User from trusted IP successfully signs into AWS Console.
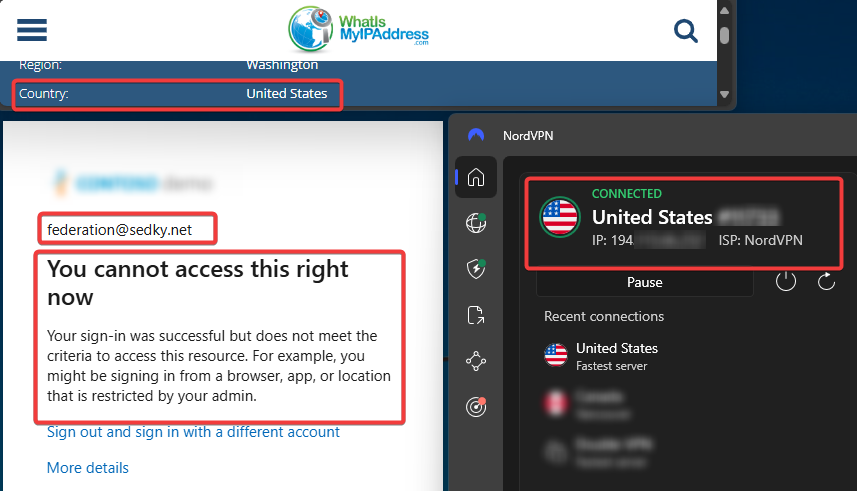
User from untrusted IP (VPN US) blocked by CA policy enforcement.
5. Security & Operational Impact
- Enforces MFA and centralized login via Microsoft Entra ID
- Eliminates static IAM users and long-lived credentials
- Role access tightly scoped to Entra security group membership
- Auditability through Entra sign-in logs & AWS CloudTrail
6. AWS Well-Architected Framework Alignment
- Security: Federation reduces attack surface and enforces identity-based policies
- Operational Excellence: Identity lifecycle is managed entirely within Entra ID
- Reliability: Trust policies and claims mapping prevent privilege drift
- Cost Optimization: Utilizes native features, no custom auth infra required
- Performance Efficiency: SAML assertions processed with minimal overhead
7. Challenges & Solutions
- Group Claim Not Mapping: Resolved by using Entra Object ID in the claim
- IAM Trust Policy Syntax Errors: Corrected using AWS role simulator preview
- Access from US not blocked: Fixed by adding named location + CA policy
- Login loop on SSO: Cleared stale sessions and used new incognito session
8. Final Outcome
This implementation demonstrates a production-grade identity federation model between AWS and Microsoft Entra ID. All access is controlled, conditional, and tied to identity groups with audit trails in both platforms. It can be extended to multiple roles, accounts, or organizations using the same architecture pattern.
This project highlights my ability to design and implement secure, scalable, and compliant cloud identity solutions, aligning with modern enterprise standards and AWS Well-Architected principles.
📘 View Full GitHub Documentation